Welcome to the inaugural PCI Report Card. In previous Practical eCommerce report cards, we’ve always been clear about the name of the merchants we’re grading. However, when dealing with security issues, such as compliance with the Payment Card Industry Data Security Standard, some discretion is required. We’ll be talking about sensitive subjects, such as vulnerabilities on publicly-facing websites and we must keep the identity of the merchant out of the article.
Merchant X is an online retailer of photography accessories, processing both ecommerce transactions and phone orders via the Volusion hosted shopping cart. Merchant X asked Practical eCommerce to grade their site for PCI Compliance. The Payment Card Industry Data Security Standard (PCI DSS) is comprised of a set of 12 requirements for securing cardholder data. Merchants must comply with the PCI DSS and, in some cases, have that compliance validated by a certified third party Qualified Security Assessor (QSA) or Approved Scanning Vendor (ASV).
Merchant X used nCircle Network Security’s PCI Scan Service to perform their external scan. nCircle is an Approved Scanning Vendor for PCI. More information about the PCI Data Security Standard, including information about QSAs and ASVs, can be obtained from the PCI Security Council.
Based on the information submitted by Merchant X regarding their volume of credit card transactions and storage of customer credit card data, we believe them to be a level 4 merchant, processing fewer than 20,000 transactions per year. The requirements for PCI compliance is as follows:
| Level | Description | Annual On-Site Audit? | Annual Self-Assessment Questionnaire? | Quarterly External Network Scan? |
| 1 | Merchants Processing more than 6 million transactions per year or have suffered an account data compromise | Yes | Yes | Yes |
| 2 | Merchants processing between 1 million and 6 million transactions per year | No | Yes | Yes |
| 3 | Merchants processing between 20,000 and 1 million eCommerce transactions per year | No | Yes | Yes |
| 4 | Merchants processing fewer than 20,000 eCommerce transactions, or up to 1 million transactions through other channels | No | Yes | Yes |
These merchant levels apply to Visa and MasterCard. American Express has only three levels, but the requirements for compliance validation work out to be the same.
Understanding of Requirements
The requirements for PCI compliance are determined by what you do with customer credit card data and by your established merchant level. In all cases, it’s worth asking if you are required to be compliant with the PCI Data Security Standard at all. The PCI Security Standards Council provides a document called “Navigating PCI DSS” which explains “The Primary Account Number (PAN) is the defining factor in the applicability of PCI DSS requirements and PA-DSS. If PAN is not stored, processed or transmitted, PCI DSS and PA-DSS do not apply.”
Merchant X does not store or process the PAN. Their payment processing is fully handled by Volusion, who is responsible for the transmission of the PAN and associated data. Merchant X simply doesn’t have access to the cardholder data at all. In other words, Merchant X is not required to be compliant with the PCI DSS because they do not store, process or transmit cardholder data electronically. The small number of telephone orders that Merchant X processes are not handled electronically.
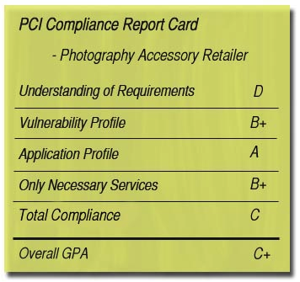 Merchant X received a D for their understanding of the requirements because they simply didn’t ask about the overall applicability of PCI DSS in the first place. Additionally, Merchant X initiated an automated scan against their payment gateway, which they aren’t authorized to scan. In order to do so, Merchant X had to affirm that they are authorized to scan that website. While it’s not likely that the gateway in question would take any action for this type of scan, there can be legal repercussions to scanning someone else’s website. The payment gateway is responsible for its own PCI compliance, and merchants should check. You can validate that your service provider is VISA certified at Visa’s website.
Merchant X received a D for their understanding of the requirements because they simply didn’t ask about the overall applicability of PCI DSS in the first place. Additionally, Merchant X initiated an automated scan against their payment gateway, which they aren’t authorized to scan. In order to do so, Merchant X had to affirm that they are authorized to scan that website. While it’s not likely that the gateway in question would take any action for this type of scan, there can be legal repercussions to scanning someone else’s website. The payment gateway is responsible for its own PCI compliance, and merchants should check. You can validate that your service provider is VISA certified at Visa’s website.
Despite determining that the PCI DSS isn’t applicable for Merchant X, it’s well worth evaluating the other report card criteria.
Vulnerability Profile
PCI compliance requires that merchants address any vulnerabilities on their publicly available websites that score 4.0 or higher base score on the Common Vulnerability Scoring System (CVSS). CVSS measures the risk and impact of a vulnerability and provides a numeric score between 0 and 10. More information on CVSS can be obtained here: http://www.first.org/cvss/
While Merchant X scanned a payment gateway they weren’t supposed to, their site in particular is in fairly good shape with only one vulnerability that requires action to be compliant. Merchant X uses a third party hosting company in addition to Volusion, it’s hosted shopping cart. On this third-party web server, Microsoft IIS 6.0, is configured to support encryption keys that are less than 128bits in length. The length of the encryption key is a determining factor in the strength of the encryption itself, and less than 128bits is considered only minimally secure. Merchant X may not be able to do anything about this condition, depending on their hosting setup. It’s entirely possible that the hosting provider is responsible for this server configuration and would need to make the necessary changes to remediate the vulnerability.
Merchant X earned a solid B+ here for keeping their site secure.
Application Profile
PCI requires that merchants keep the applications on their publicly available IP addresses at supported versions with necessary patches. There’s no common scoring system like CVSS for application obsolescence, so it’s up to the Approved Scanning Vendor to determine which applications are no longer supported.
Merchant X is using Microsoft IIS 6.0 on Windows Server 2003, as provided by their third-party hosting company. Both the operating system and the applications on this server are currently supported by the software vendor, in this case, Microsoft. No outstanding patches were discovered either. In other words, Merchant X, through its third-party hosting company, has done a great job in keeping their externally facing applications up to date, or in selecting a hosting provider who does so, and deserves an A.
Only Necessary Services
Unnecessary services can often be the source of undetected vulnerabilities or information that attackers can use to compromise a system. PCI requires that only necessary services be running on hosts in order to minimize that risk. While a third party such as Practical eCommerce or nCircle (the Approved Scanning Vendor) can’t be 100% sure that a service is unnecessary, there are some services that rarely serve a business need on a public website. This includes less secure services such as telnet, which shouldn’t be offered to the Internet at large. Common services like email should be appropriately segregated onto a different server.
Merchant X received a B+ here because while they’re well locked down, they are running multiple services on this IP address. Specifically, HTTP for the web server and Microsoft IIS FTP as a file transfer protocol server. Again, the hosting provider may be in control of these services and, in fact, HTTP is clearly necessary for running a website, and FTP is most likely used for updating content to the website. The server could be locked down further, but no vulnerabilities were discovered in the FTP service.
Total Compliance
Total compliance is difficult to grade in this situation. On the one hand, Merchant X deserves an A+ for taking proactive steps to assure PCI Compliance, even though it’s not applicable. On the other hand, Merchant X didn’t fill out the self-assessment questionnaire (SAQ) at all, which is probably a better first step than conducting a network scan. The SAQ can help a merchant determine if and how the PCI DSS is applicable to their situation. SAQs can be obtained directly from the PCI Security Standards Council or from an ASV.
Ultimately, we split the difference and gave Merchant X a C on total compliance. The effort was good, but the steps taken weren’t in quite the right order.
PCI Report Card
Retail Photography WebsiteUnderstanding of Requirements: D
Vulnerability Profile: B+
Application Profile: A
Only Necessary Services: B+
Total Compliance: COverall GPA C+
Request a PCI compliance site grade by emailing pci.report@practicalecommerce.com.




