In web development, a “cookie” stores basic user information on the user’s own computer, potentially improving the browsing experience and even making visitors to an ecommerce site feel more welcome.
Cookies are often used to save a visitor’s username and password so that the visitor does not have to sign on for each and every visit. Cookies can be used to track information that leads to making better product recommendations in an online store or to help offer special prices and discounts to loyal shoppers. Cookies can also store user preferences so that a site remembers how the user likes things arranged.
To some, cookies can also seem a bit vague or even dangerous. In fact, technical author Kevin Yank wrote in his book, Build You Own Database Driven Web Site Using PHP & MySQL that cookies are one “of those mysterious technologies that are almost always made out to be more intimidating and complex than they really are.”
A Cookie is a Name-Value Pair
To help understand what a cookie is, it may be useful to imagine opening a word processor, like Notepad, Google Docs, or Microsoft Word. Next, type some words or even a sentence or two. Then save the file in text format, giving it a name like name.txt. The words and sentences typed into the document represent the value of the file and, as you might guess, the file’s name, name.txt, is its name. This relationship (name-value pair) is almost directly analogous to a cookie, which is a text file with some value and a specific name by which it can be referenced.
A cookie’s value might be something easy to understand and read, like a username, or it could be a token, which is a series of numbers and letters that reference something on a specific web server or in a web database. The cookie’s value might match a field in a database. Related fields would hold customer information, so by getting the cookie’s value, the sever also has access to the content of the related fields.
Here is an example cookie from the Puma website. Its name is s_vi: [CS]v1|25E09CBC05010BAE-400001168000F7A8[CE].
In all likelihood, this token will access some stored data — like which products the user looked at or how long the user lingered — on the Puma web server.
If the Puma visitor were a returning customer, this cookie and its value might be used to restore items to an abandoned shopping cart or remember the visitor’s account credentials. It is possible that this cookie could, by enabling the site to address the shopper by name, make the visitor feel more welcome.
This next example is a cookie from a WordPress blog. This cookie’s name is BX : 0m6c3996l1eum&c=3&s=g6.
This cookie’s value might be used to append a URL and turn on or off some set of features.
Here is another example cookie. This one is from Alienware. Its name is AlienwareInfo: AlienwareInfo.
Because of its simplicity, it may be that Alienware is using this cookie to determine if a user has been one the site before and in combination with other cookies also set during the user session.
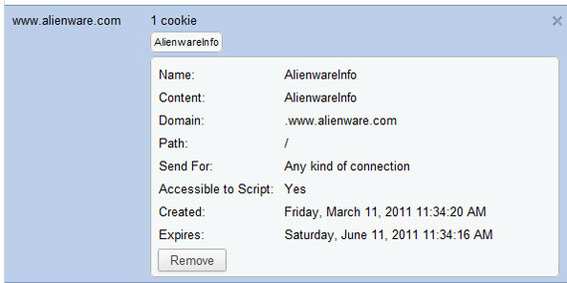
The Alienware cookie, which is shown here in Google Chrome, is basic and human-readable.
Browsers also store other information about cookies. For example, cookies are generally available to a single domain and the browser — such as Microsoft Internet Explorer (IE) 9, Mozilla Firefox, Google Chrome, or Apple Safari — keeps track of this proper domain.
Cookies also have specified expiration dates, which the browser monitors, and cookies may allow or disallow script access. For example, a JavaScript on the Alienware website would be able to see the content of the cookie shown above because “Accessible to Scripts” was allowed. If this had been turned off when the cookie was created, the cookie would only be accessible from the Alienware web server and not to any client-side (browser) script.
Finally, it is important to remember that cookies are stored on the user’s own computer, phone, or tablet.
What Cookies Do
Cookies store data. They give a website long term memory, generally without putting the user or the user’s privacy — more on this below — at risk. Because a website can “remember” things about the user, the site can make things easier.
Perhaps the simplest example to understand is logging in to a website. If cookies did not exist, each time a user visited a website, that user would have to log in, even if those visits were just a few minutes apart. In a worst-case scenario, a site without cookies might require you to log in each time you opened a new page. Such a site would not be able to remember anything about the visitor from one session to the next or even one page to the next in some cases.
Login data is just the tip of the proverbial iceberg when it comes to cookies, which make many of the Internet’s most widely used and appreciated features possible — wish lists, product comparisons, and product recommendations, to name a few examples. And, it is worth noting that nearly every website, particularly for ecommerce, uses cookies.
Most Cookies are Safe
There has been a lot of discussion in publications, on forums, and even in legislative halls about cookies and privacy, or cookies and web security. Many Internet users ask, “Are cookie’s safe?”
To again reference Kevin Yank’s book, “cookies in and of themselves are incapable of compromising a user’s privacy.”
“There are many common misconceptions about cookies,” wrote Tom Negrino and Dori Smith in their book, JavaScript for the World Wide Web. “So it’s important to note what you can’t do with them: you can’t get any real information about the user such as their email address; you can’t use cookies to check out the contents of their hard disks; and cookies can’t transmit computer viruses. A cookie is just a simple text file on the user’s hard disk.”
Cookies, which cannot be executed like scripts, are relatively benign and unquestionable helpful. However, there are some uses of cookies that users might not be happy about.
Third Party Cookies and Other Concerns
Cookies are supposed to help a single website remember something about a particular user in order to improve that user’s experience, provide information to the site, or enable features or measurement. When a cookie is set, the browser records the host server (domain), and the next time the user visits the host, the browser shares the cookie data.
When a user visits a webpage like SomeSite.com, you might think that the only web server providing data and setting cookies would be SomeSite.com, but that might not be the case. If the site includes social media widgets, ad network script, or web tracking and analytics content, there may be several web servers interacting with the browser, and each of these servers may be setting cookies.
In the image below, there may be six web servers or more contributing to the page and, potentially, setting browser cookies. The web servers involved include the domain’s own for adding most of the page content, the ad network that is serving up the Microsoft ads shown, and the various social media sites that have widgets on page — Facebook, Twitter, Google Buzz, and Digg.
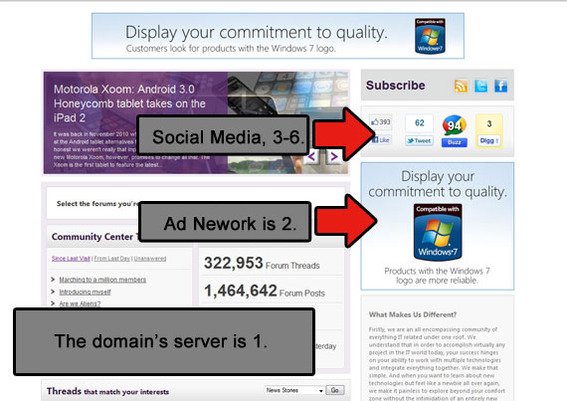
This page may have as many as six web servers providing content and setting cookies.
It is possible — if not likely — that each of these servers would set or update a cookie. In fact, in the example page displayed above there was an ad network cookie set for rotator.adjuggler.com. If a user visited another site using the identical ad network, the ad network’s server might be able to collect information from the existing cookie and, thereby, aggregate user information from across more than one domain.
This type of cookie, one that might appear on several domains from an ad network or the like, is called a “third party cookie.” It has raised valid privacy concerns. In fact, there has been some indication that legislators could make using third party cookies illegal in some instances. Also, the specifications that describe cookies — the Internet Engineering Task Force’s RFC 2109 and RFC 2965 — encourage browsers to refuse third party cookies by default. However, that is not generally the case.
Other potentially distasteful uses of cookies, include so-called zombies, which are cookies that do not expire, but are rather reset by a script. Some Flash cookies — see “An Introduction to Flash Cookies; How to Manage Them,” our recent article on that topic — could be considered to be zombies. When used across multiple domains, zombies could potentially be a privacy concern.
Finally, there are also so called super cookies that are set for domain endings, like .com rather than SomeSite.com. Fortunately, most modern browsers will refuse this sort of cookie.
Cookies, then, are generally safe. They cannot spread a virus, and generally won’t share too much information unless they are used by a third-party. From the site owner’s perspective, choose the third party providers you use wisely in order to protect your customers.
Setting, Reading, and Deleting Cookies
The code used to set a cookie is generally simple. The following example is PHP.
<?php
$value = 'cookie value';
setcookie('my_cookie', $value, time()+3600);
?>
Above, the first line sets a variable to “cookie value.” Next, a function named setcookie() is used to send the cookie to the web browser. The setcookie() function has three parameters in this example. The first parameter passes the cookie’s name. In this case, that name is “mycookie.” The second parameter uses to variable created above to pass the cookie’s value. The third parameter sets the cookie’s expiration, which in the example is one hour (3,600 seconds) from the current time (time()_). PHP can add more complex cookie data if needed, but that is beyond this article’s scope.
In JavaScript, the code for setting a cookie is also simple, using the pages cookie property.
Document.cookie = 'my_cookie=cookievalue; expires=Fri, 1 April 2011 10:10:10 UTC'
In this JavaScript example, the cookie name and value are passed as a pair, followed by the expiration date. Again, more complicated implementations are possible when required.
To read a cookie, you may simply reference it. The example below is a simple bit of JavaScript that will read (get the value of) a cookie.
var cookieContent = document.cookie.split('=')[1];
Again, this is a simple example, but it should return cookievalue.
In PHP, reading a cookie might look like the following.
$cookie_example = $_COOKIE['my_cookie'];
The variable $cookie_example would hold the cookie’s value.
In both the JavaScript and PHP examples shown, you would want some additional code that would test to determine if the cookie already existed. So don’t paste the above examples into a site; they are simply representative of setting cookies in these languages.
Finally, to delete a cookie, set is expiration date to sometime in the past.
This code will work on any browser, and can be initiated from just about any web server. Even hosted ecommerce platforms, which restrict access to server side code like PHP, may accommodate JavaScript-based cookies.
Summing Up
Cookies are name-value pairs that give a website “memory” so it can recognize a returning visitor. Cookies make many useful web features possible. And cookies work across all web browsers.
Although it is possible to misuse a cookie, the technology itself is benign and actually quite secure.
Finally, cookies are in wide use. Nearly every website uses cookies to improve customer experience.




