Microsoft announced a major vulnerability in all versions of the popular Internet Explorer (IE) web browsers that makes it possible for malicious websites to hijack a visitor’s computer.
Microsoft said that it did not believe that any serious criminals were either using or previously were aware of this serious vulnerability. Rather, Metasploit, which is a project aimed at providing information and tools to computer security experts, apparently discovered the weakness in IE.
Protect Your Computer
Microsoft has also suggested a way to protect your computer should you choose to keep using IE.
To eliminate this new vulnerability, you’ll need to download Microsoft’s Enhanced Mitigation Experience Toolkit (EMET). EMET is a utility created specifically to help protect systems on all sorts (browser, Windows Desktop, or even servers) from common security threats. Specifically, you’ll need to use EMET to protect iexplore.exe.
You should make sure that you get EMET version 2.0 since it will be the one to patch the IE vulnerability announced and since it has a graphic user interface. Earlier versions of EMET required users to enter command line code.
Once downloaded, you will need to run Setup.msi. Your computer may warn you that this type of file can be dangerous, which it can be. But if you are downloading this directly from Microsoft you will be fine.
Run Setup.msi to begin installing EMET.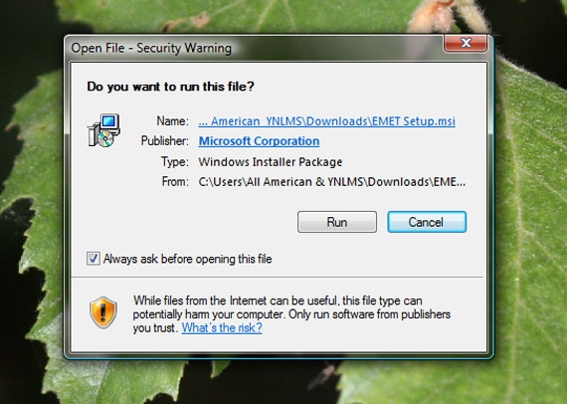
Next, EMET will open a “Wizard” screen explaining that you will be guided through the steps needed set up the software.
EMET provides a explanation of what will happen next.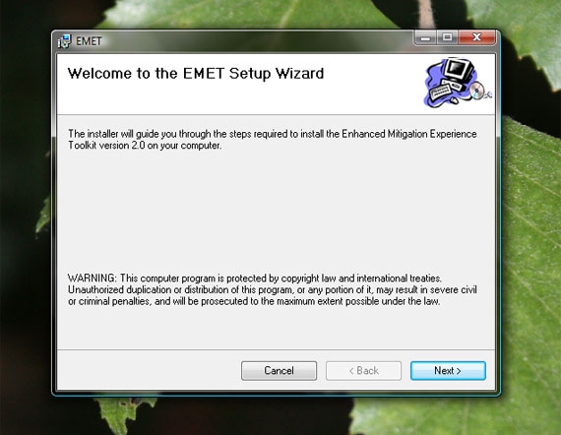
EMET will next ask where you want it to be installed on your system and whether or not you want to install it for the current user only or for every user account on the machine.
EMET gives you the option to select where it is installed.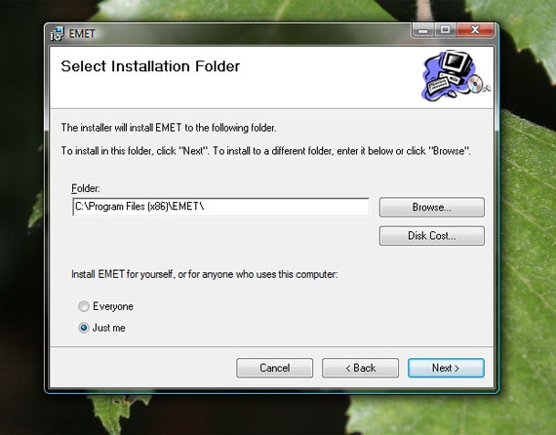
EMET does require you to affirm a software license agreement. This is standard for nearly all software.
EMET asks you to affirm its software license agreement.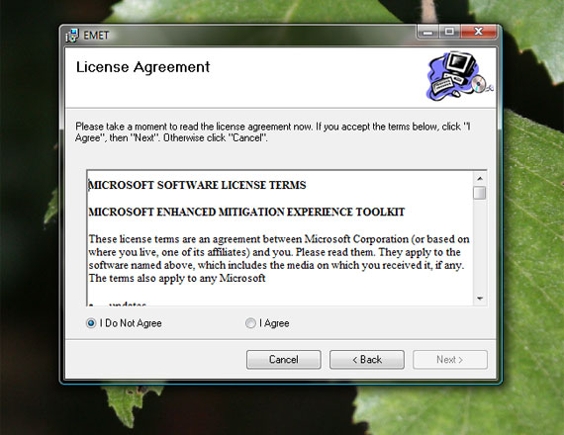
With the license agreement accepted, you will be asked to confirm the installation.
EMET asks you to affirm its software license agreement.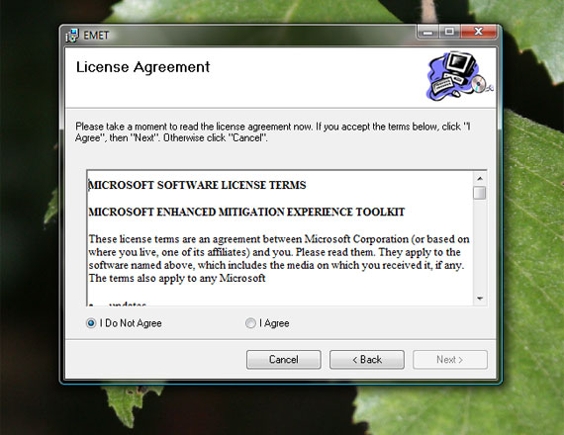
The actual installation process should be pretty quick.
EMET gives you a confirmation screen before consummating the installation.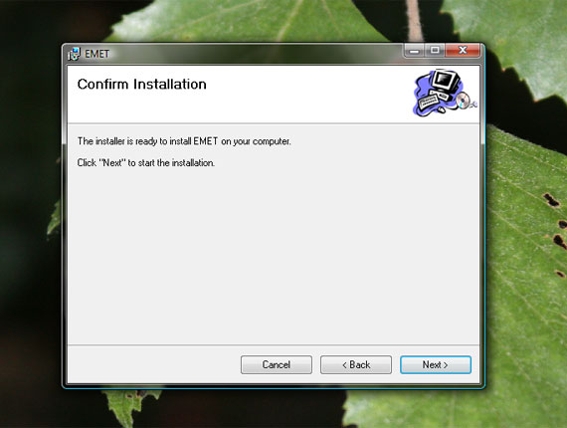
Now you will need to open the EMET interface. Navigate to your “Start” menu, “All Programs,” and then the “Enhanced Mitigation Experience Toolkit.” You may also want to review the included Users Guide if you have questions or concerns.
EMET installs quickly.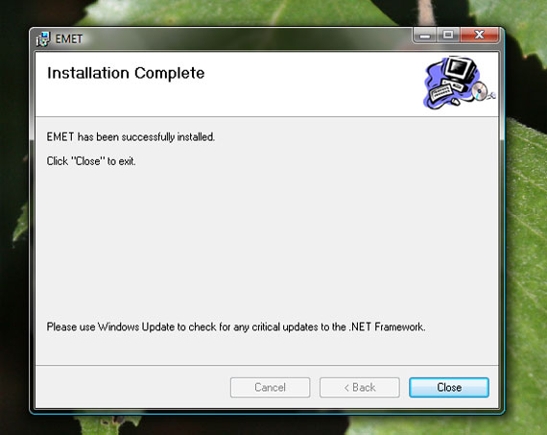
With EMET open (and IE open), you’ll just need to confirm that iexplore.exe has a green check next to it in the EMET control panel. If this is the case, you will have plugged the aforementioned IE vulnerability.
Open EMET from the Windows Start Menu.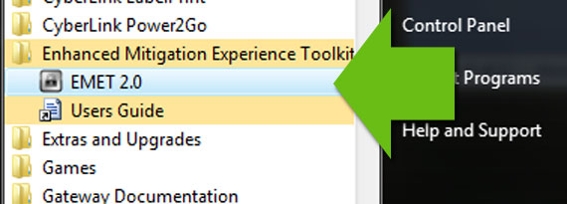
The steps above were completed on a machine using Windows Vista, so there may be minor variations if you computer is using XP or Windows 7. Finally, Microsoft has also created a video explaining EMET, which is republished below.
How This Vulnerability Works
In simple terms, it is possible to bypass Microsoft IE’s built-in security using basic tags found on nearly every website. Once bypassed a cyber-criminal can seize memory on your computer and load just about any sort of software on that memory that they wish. For example, a “key logger” might be installed to monitor every key a user presses. Combined with cookie or session data, a criminal could get passwords to just about any website, including banking sites.
Here is how Microsoft described the threat in an announcement on its TechNet blog.
“In a few words,” wrote Microsoft Security Software Engineer Fermin J. Serna, “Internet Explorer loads mscorie.dll, a library that was not compiled with /DYNAMICBASE (thus not supporting ASLR [Address Space Layout Randomization] and being located always at the same base) when processing some HTML tags. Attackers use these predictable mappings to evade ASLR and bypass DEP [Data Execution Prevention] by using ROP (return oriented programming) gadgets from these DLLs [dynamic-link libraries] in order to allocate executable memory, copying their shellcode and jumping into it.”
Implications for Web-Based Businesses
This IE vulnerability should have no effect on legitimate online businesses, except perhaps to see a change in browser share, as some users may opt to avoid IE altogether, given its history of repeated and often exploited vulnerabilities.
Summing Up
Every browser company faces security vulnerabilities, and as a best practice users should always try to update their browsers to the most recent version available. In this particular case, Microsoft has done exactly what a responsible software company should do. It is important that we commend them. If you’re a loyal IE user, you probably won’t want to switch browsers just because of this issue.




